2017
Project Title:
Opportunistic Network for Proof of Location
Supervisors:
Dr. Lionel Wolberger , Platin.io
Description:
Platin.io brings location to the world of decentralization, supplying this missing piece. When Proof of Location (PoL) is provided via the Platin blockchain, a transaction fee is charged in “Platin” (PTN) that also serves as the “gas” for fueling proof of location requests. This enables for example to transfer virtual money to a certain location.

Project Title:
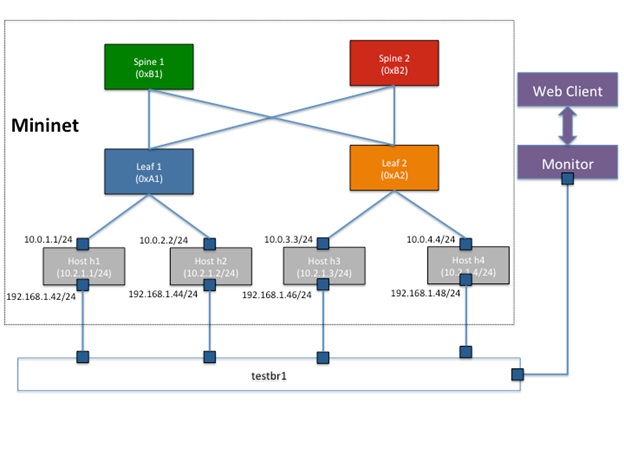
OpenDaylight NETCONF/YANG Adapter for VPP
Students:
Sivan Ben-Haim, Nir Chachmovitz
Supervisors:
Charles Eckel, Cisco
Description:
All NETCONF/YANG-enabled network functions - whether physical or virtualized - can be controlled by an OpenDaylight (ODL) SDN controller so long as an appropriate device adapter has been installed in the ODL controller. That ODL device adapter (or southbound plugin) can be generated from the network function's YANG model, and can be completed with Java programming.
Project Title:
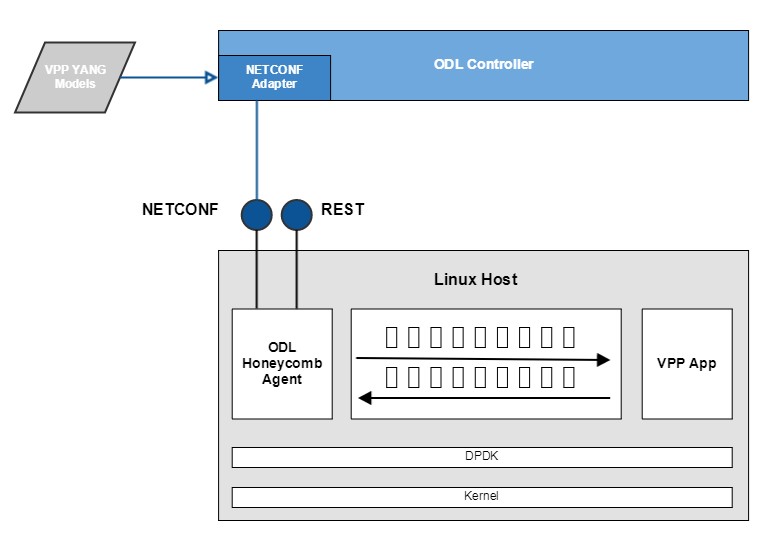
Italian Performance Monitoring Method
Supervisors:
Itzik Ashkenazi
Description:
Nowadays, most of the traffic in Service Provider’s networks carries contents that are highly sensitive to packet loss, delay and jitter. In this sense, Service Providers need methodologies and tools to monitor and measure network performances with an adequate accuracy, in order to constantly control the quality of experience perceived by their customers and also in order to fast troubleshoot and isolate network problems.
Recently, a new method to perform passive performance monitoring was proposed by Telecom Italia. It is based on Alternate Marking (coloring) technique done on live traffic, and addresses mainly packet loss measurements.
Project Title:
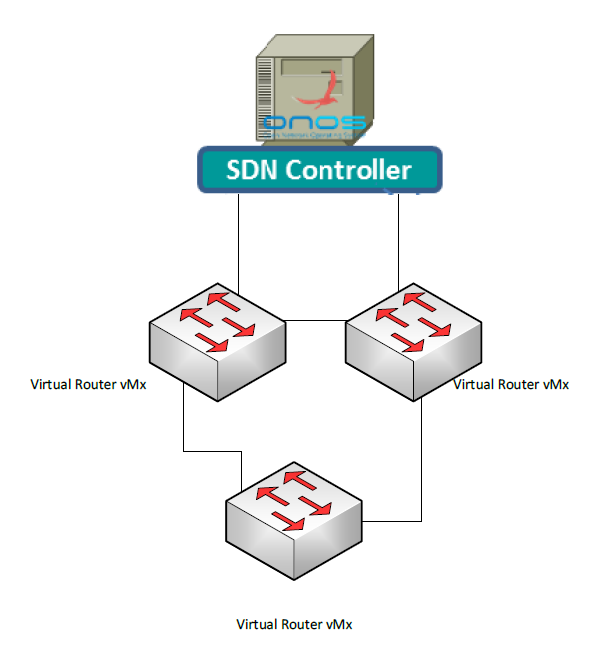
Virtual Router managed by ONOS
Supervisors:
Itzik Ashkenazi
Description:
Open Network Operating System (ONOS) is an innovative and rapidly growing open source project that already enable service providers to build real Software Defined Networks (SDN). The deployment of SDN will require ONOS to manage Virtual Routers.
The Juniper vMX Virtual Router maintains complete feature and operational consistency with physical MX Series 3D Universal Edge Juniper Routers. It runs the Junos operating system.
Project Title:
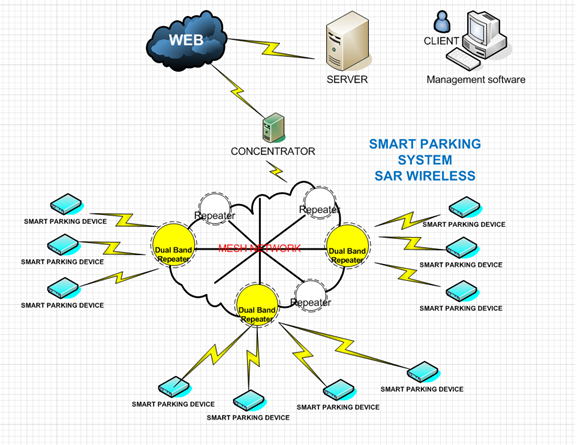
Smart IoT Parking wireless Sensor
Students:
Oved Chitayat, David Smolyanov
Supervisors:
Shai Ben-Ari, Itzik Ashkenazi
Description:
One of the fundamental requirements from a Smart Campus Transportation implementation and deployment is the ability of the campus to take responsibility and globally manage the traffic as whole inside the campus physical boundaries. This management should then serve both campus applications (such as events organizations or security needs) as well as guests that enters or plans to arrive. This can be achieved by improved monitoring and ability to supply on-line valuable information gathered from Internet-of-Things (IoT) sensors and gateways that are installed all over the campus area.
Project Title:
TCP Congestion Control new Architecture - PCC
Supervisors:
Itzik Ashkenazi
Description:
Since its deployment about 27 years ago, TCP’s congestion control architecture has been known for its poor performance and un-fairness on noisy links and the rapidly changing networks.
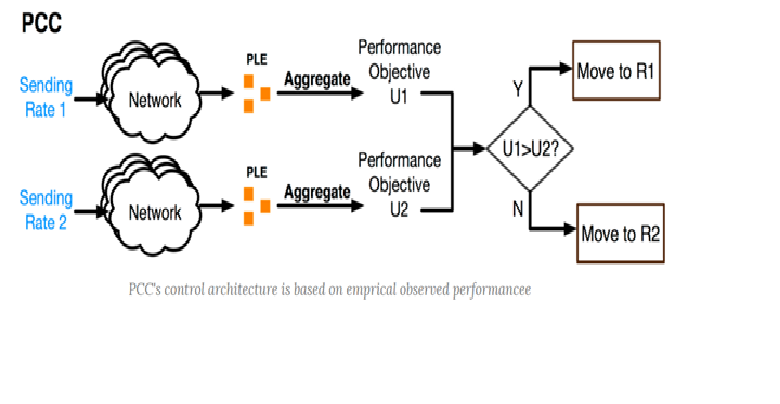
Lately, new congestion control architecture was proposed to improve the TCP performance over modern networks: Performance-oriented Congestion Control (PCC).
PCC's goal is to understand what rate will improve performance based on live experimental evidence. It tries out a high and low send rate, collects information on RTT, BW, and packet drops and then uses a fitness function to determine what to do.
Project Title:
TCP Congestion Control new Architecture - BBR
Supervisors:
Itzik Ashkenazi
Description:
By all accounts, today's Internet is not moving data as well as it should. The main root cause of it is the design choice made when TCP congestion control was created in the 1980s—interpreting packet loss as "congestion". Since its deployment about 27 years ago, TCP’s congestion control architecture has been known for its poor performance and un-fairness on noisy links and the rapidly changing networks.
Lately, new congestion control architecture was proposed to improve the TCP performance over modern networks: Performance-oriented Congestion Control (PCC) and Bottleneck Bandwidth and Round-trip propagation time (BBR).
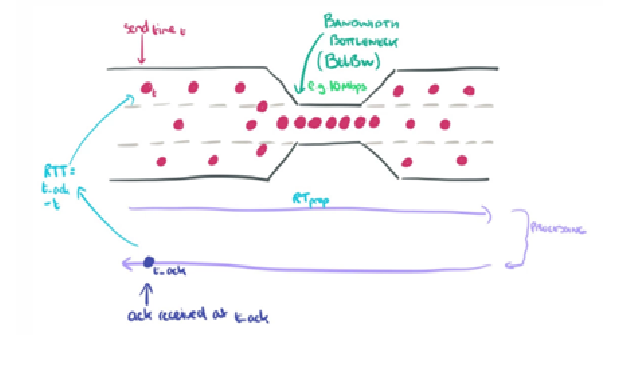
BBR is developed by Google. Its main concept is to continuously track the slowest link (bottleneck) bandwidth in each direction of the TCP connection as well as the RTT of the connection.
Project Title:
BGP protocol deviations in routers
Supervisors:
Dr. Gabi Nakibly
Description:
Routing protocols such as OSPF and BGP have open standards (published in RFCs), however commercial routers (e.g. Juniper and Cisco) that implement those protocols may deviate from those standards (deliberately or inadvertently). Such deviation are important to identify from a security point of view as they may be a pose a security vulnerability. We would like to discover those deviations. The problem is that commercial routers are closed-source so it is difficult to directly analyze the router’s implementation.
Project Title:
SDN In-Band Boot Strapping
Supervisors:
Itzik Ashkenazi
Description:
In traditional networks, the control software is distributed across all devices, which run routing protocols to compute forwarding state. An advantage of this design is that legacy networks can use the in-band ports for the control plane.
In contrast, Software Defined Networking (SDN) is based on the separation of the control plane from the data plane. Because of that, most SDN deployments today use out-of-band control and the controller configuration parameters (for example: Controller IP, Controller port #) in each switch in those deployments are static.
Such way of deployment is a major obstacle and operators are looking for a way where both the control and data planes will be transmitted on the same channel (in-band mode) and there will be no need to statically configure each deployed switch.
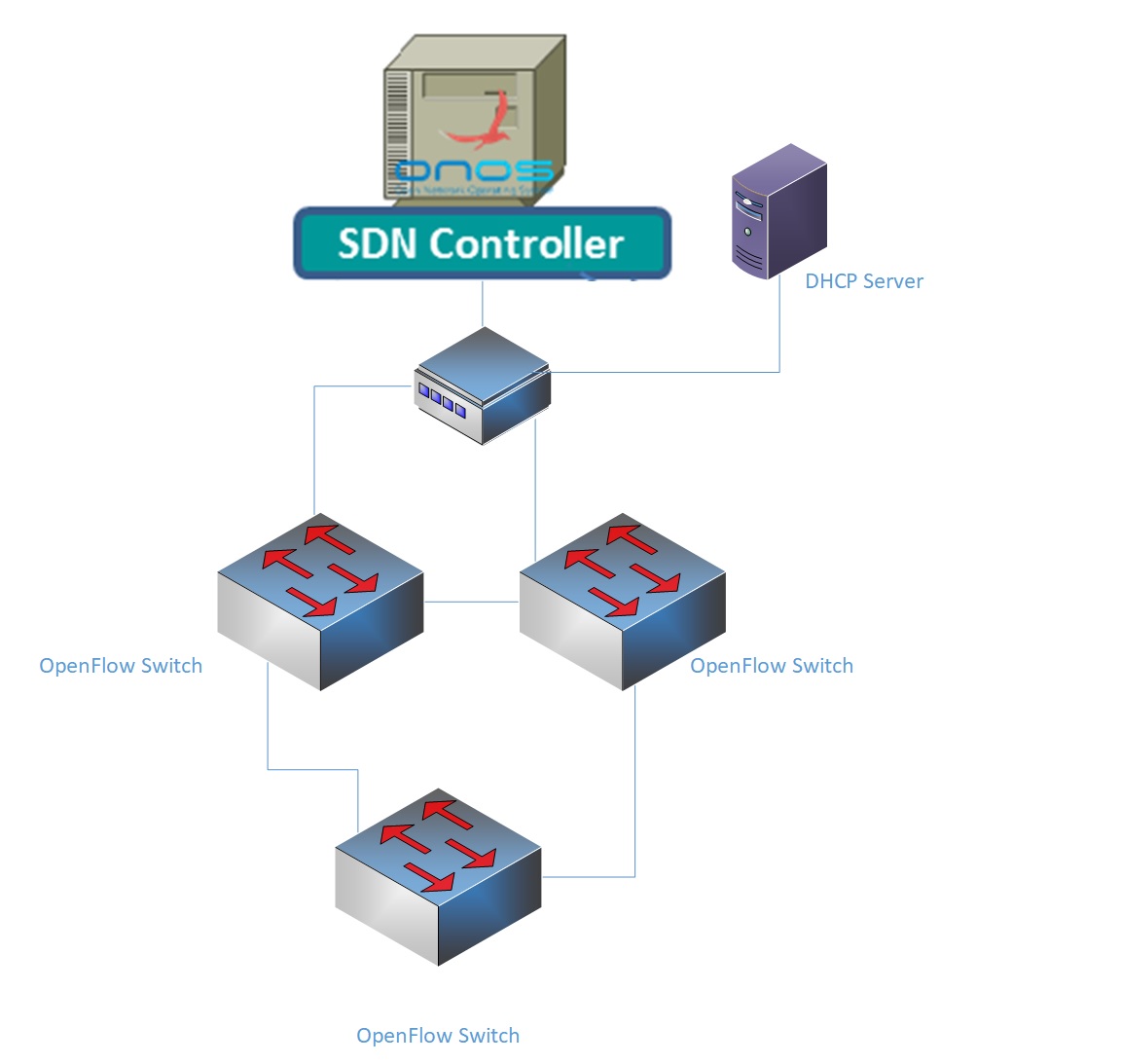
Project Title:
Automated Service Ordering
Students:
Rami Geraisy, Wissam Abu Sini
Supervisors:
Ran Yazdi (Amdocs)
Description:
The project will revolutionize the way network services are ordered between telecom companies. It will turn what is a weeks long process into a modern API-driven operation and save millions of dollars in the process. The working prototype built will be used as a basis for ordering in all international telecom companies for the next 20 years.
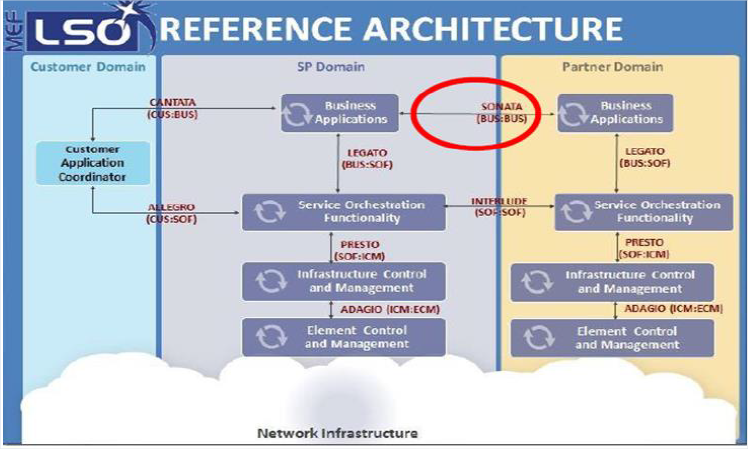
Project Title:
MEF Point-to-point Ethernet Service
Students:
Muhammad Abed, Rand Hreish
Supervisors:
Daniel Bar-Lev (MEF)
Description:
The MEF is a collaborative code and specs development organization that starting in 2001 defined Carrier Ethernet and helped build the global Carrier Ethernet market now valued at $80Bn. MEF has 210 member companies, of which 130+ are the world’s leading service providers, including AT&T, Verizon, Deutsche Telekom, BT, China Telecom, Cisco, Huawei, Ciena and many Israeli companies such as ECI, RAD, Telco Systems and Amdocs. Carrier Ethernet services defined by the MEF and widely adopted by the telecoms industry include E-Line, E-LAN, E-Tree, E-Access and E-Transit
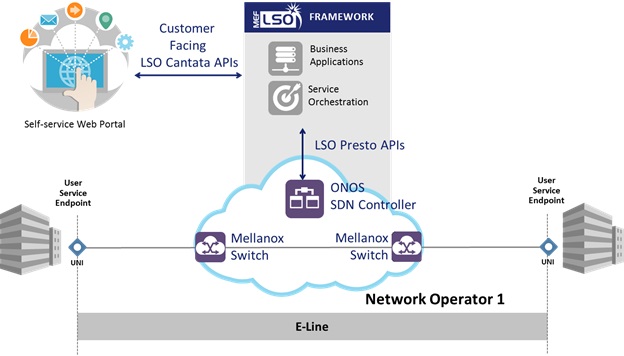
Project Title:
Connection Tracking (CT) - Open Virtual Switch (OVS) Offload
Supervisors:
Dr. Tal Anker, Mellanox
Description:
Today’s Carrier Ethernet architecture is undergoing the biggest transformation since the beginning of the internet. Video, mobile and cloud usage is driving huge growth in traffic while the constantly changing traffic patterns requires ability to introduce new services quickly. This led the creation of Networking Function Virtualization (NFV), which defines the specifications for Virtualized Network Function (VNF).
VNF is a software implementation of a network function such as routing or firewall. Each such VNF runs in a virtual machine (VM). The VMs are created in a compute blade or in a high scale server – unusually called the host device. The VMs are located on top of the host’s Hypervisor that uses Open Virtual Switch (OVS) to switch the data traffic to/from each VM/NFV and also to chain the traffic between them.
OVS is designed to operate under Linux Operating System and uses its kernel services to perform various operational-related functions. One of the frameworks that the kernel provides is NetFilter that offers various operations like packet filtering, Network Address Translation (NAT) and more. One of the important features built on top of the Netfilter framework is Connection Tracking (CT). CT allows the kernel to keep track of all logical network connections, and thereby relate all of the packets which may make up that connection.
When CT is used along with OVS, using an advanced Network Interface Card (NIC) to handle the connections can help to offload OVS.
Project Title:
VxLAN EndPoint with INT support
Supervisors:
Itzik Ashkenazi
Description:
Virtual Extensible LAN (VXLAN) is an encapsulation method to extend layer 2 traffic over a layer 3 or IP-based network. It is designed to provide the same Ethernet layer 2 network services as a virtual LAN (VLAN) does today, but with greater extensibility and flexibility. Compared to VLAN, VXLAN can extend layer 2 segments across the data center network by using MAC-in-UDP encapsulation scheme.

Project Title:
Analysis of the QUIC protocol
Description:
QUIC is a new transport layer designed by Google to replace TCP. It offers reduced latency and higher throughput as compared to TCP. Although the protocol is already widely used by Google’s services and Google’s Chrome the protocol design and deployment is still nascent. The standard of the protocol is being written these days by the IETF. However, it is obvious that the Google implementation has many more details as compared to the standard’s draft in its current form.
Project Title:
Security Policies Tracking
Students:
Gal Berger, Evgeny Shapiro
Description:
Cisco TrustSec solution enables deployment of security policies into organization’s network. The policies are enforced by the network infrastructure such as routers and switches. The policies define the type of traffic that is allowed in the network and whether traffic of some employee in an organization is allowed to reach various resources in the network (for example policy can define that in the network of the university a student can access only the servers in the computer science faculty lab and cannot access any other computers in the university).
The network security policies are dynamic and are obligated to changes. As a result the network infrastructure which enforce the policies maintains different policies at a given time.
Project Title:
Identify Abnormal User Network Access
Description:
Cisco Identity Service Engine (ISE) is responsible to authenticate and authorize users that login into an organization networks such as in universities for example (only students and/or staff can login the network with different privileges). Once some user access the network ISE collects various information about the user such as whether the user access the network from wireless connection or wired. The location of the user, the user IP address, the user MAC address, the OS type the user uses (iOS, Android, Windows etc.) and more

Project Title:
Power efficiency SDN application
Description:
The current architecture of telecom and data networks is based on the IP protocol stack, where the routing is made by distributed hop by hop decisions over single data packets.
This approach is beginning to show some limits in terms of performance, flexibility and scalability due to the exponential growth of data traffic that we have been experiencing for some years. The requirements on the different traffic types range from high throughput to low latency, from high user density to high availability, from low power consumption to high reliability. The fulfillment of such a wide variety of requirements asks for a quite different network architecture, where adaptively is fundamental.
Project Title:
BGP Deviations In Routers
Students:
Yair Cohen
Supervisors:
Dr. Gabi Nakibly
Description:
Routing protocols such as OSPF and BGP have open standards (published in RFCs), however commercial routers (e.g. Juniper and Cisco) that implement those protocols may deviate from those standards (deliberately or inadvertently). Such deviation are important to identify from a security point of view as they may be a pose a security vulnerability. We would like to discover those deviations. The problem is that commercial routers are closed-source so it is difficult to directly analyze the router’s implementation.

Project Title:
INT on P4 Software Switch
Description:
In-band Network Telemetry (INT) is a new framework designed to allow the collection and reporting of network state, by the data plane, without requiring intervention of additional control plane protocols. Data packets are instrumented with INT header fields that contain “Telemetry Instructions” to INT-capable network device. The instructions tell the devices what Telemetry data to collect and the collected data is written into the forwarded data packets.
INT data that can be collected includes: switch IDs, Input/Output Port IDs, Hop Latency, Queue Occupancy, In/Out Timestamps and more. Such telemetry data provides immense value in networks in general. It enables real-time debugging of network issues as well as “self healing” networks.
Programming Protocol-independent Packet Processor (P4) is a high-level language that can be deployed in the future into Software Defined Networks (SDN) and can actually serve as an alternative to OpenFlow that is currently used – due to its flexibility and ability to support emerging new protocols such as INT.