2020
Project Title:
MANET Traffic Performance Prediction
Supervisors:
Itzik Ashkenazi,
Description:
Mobile Ad-hoc NETworks (MANET) is a communication platform for wireless first response units that creates a temporary network without any help of any centralized support. MANET is characterized by its rapidly changing connectivity and bandwidth over the communication links.
Mobile Ad Hoc Network is a collection of wireless hosts that creates a temporary network without any help of any centralized support. At the same time, the application runs on the units often requires strict availability of end to end bandwidth and delay.
It is essential to be build an optimization tool that will be able to predict the traffic bandwidth or the delay performance once the network topology changes or a new application starts running. Developing such tool requires network modeling. Nowadays, network models are either based on packet-level simulators or analytical models (e.g., queuing theory). Packet–level simulators are very costly computationally, while the analytical models are fast but not accurate. Hence, Machine Learning (ML) arises as a promising solution to build accurate network models able to operate in real time and to predict the resulting network performance according to the target policy, i.e maximum bandwidth or minimum end-to-end delay.
Recently, Graph Neural Networks (GNN) have shown a strong potential to be integrated into commercial products for network control and management. Early works using GNN have demonstrated capability to learn from different network characteristics that are fundamentally represented as graphs, such as the topology, the routing configuration, or the traffic that flows along a series of nodes in the network. In contrast to previous ML-based solutions, GNN enables to produce accurate predictions even in networks unseen during the training phase.
Project Title:
MPEG-DASH Proxy Live Streaming from Multiple Servers in Unstable Environment
Supervisors:
Aviel Glam (Rafael), Itzik Ashkenazi,
Description:
MPEG-DASH (Moving Picture Experts Group - Dynamic Adaptive Streaming over HTTP) is a vendor independent, international standard ratified in 2012. One of the main benefits of MPEG-DASH is reduction of startup delays and buffering/stalls during the video and continued adaptation to the bandwidth situation of the client.
Today, MPEG-DASH is gaining more and more deployments, accelerated by services such as Netflix or Google, which recently switched to this new standard. With these two major sources of internet traffic, 50% of total internet traffic is already MPEG-DASH.
The basic idea of MPEG-DASH is as follows: chop the media file into different bitrates or spatial resolutions encoded segments. The segments are provided on a Web server and can be downloaded through HTTP standard compliant GET requests where the HTTP Server serves different qualities, chopped into segments of equal length. Since the client knows its capabilities, received throughput and the context of the user best - the adaptation to the best bitrate or resolution is done on the client side for each segment.
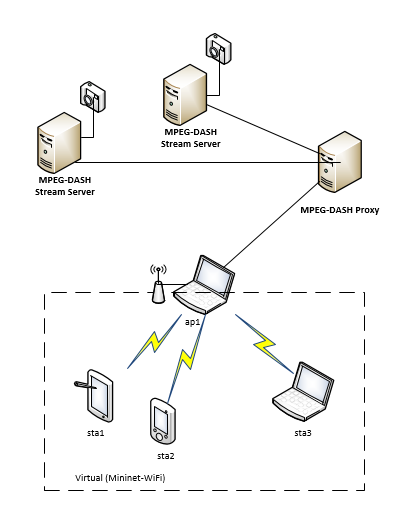
In certain cases, there is a need for multiple clients to receive the same video stream. Since the client’s bandwidth and connection quality can vary, the challenge is to stream to each client the best possible quality, using MPEG-DASH Proxy, while maintaining live streaming. A greater challenge is to support in addition cases where there are multiple servers and the proxy-servers connection is unstable.
Project Title:
IoT Cyber Attacks Self Detection
Supervisors:
Aviel Glam (Rafael), Itai Dabran (ICST), Itzik Ashkenazi (LCCN)
Description:
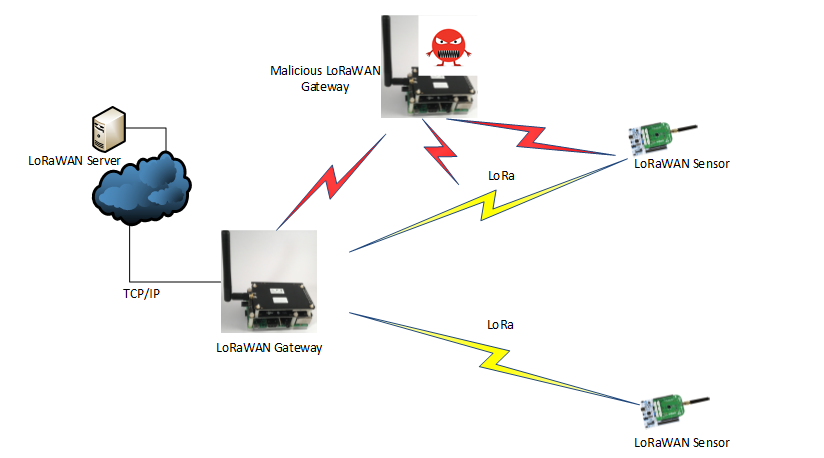
Low-power WAN (LPWAN) is a wireless wide area network specification for Internet-of-Things (IoT) deployments that interconnects low-bandwidth, battery-powered sensors with low bit rates over long ranges.
To meet the challenges of long range, low power consumption and secure data transmission, the sensors are based on LoRa Technology and on LoRaWAN media access control (MAC) layer protocol that manages communication between LPWAN sensors and the Gateway.
LPWAN based LoRaWAN is vulnerable to 2 cyber attack types: Malicious Gateway and sensor flooding attack. Malicious LoRaWAN Gateway can track the sensors-gateway downlink-uplink traffic pattern and then disrupt the traffic. Sensor flooding attack can be generated by multiple coordinated malicious LoRaWAN sensors that can generate traffic simultaneously and so cause the LoRaWAN server to mal function. LoRaWAN gateways should be able to self-detect such attacks and avoid LPWAN collapse.
Project Title:
Real-Time Traffic Classifier on Mellanox Switch– using P4
Supervisors:
Alan Lo (Mellanox), Itzik Ashkenazi
Description:
Traffic classification, the categorization of network traffic into appropriate classes, is important to many applications, such as quality of service (QoS) control, pricing, resource usage planning, malware detection, and intrusion detection. Because of its importance, many different approaches have been developed over years to accommodate the diverse and changing needs of different application scenarios. In particular, the growing trends of Internet traffic encryption and an increase Virtual Private Networks (VPNs) and The Onion Router (ToR) usage, raise additional challenges to network traffic classification.
Using Deep Learning (DL) methods, we managed to train a Convolutional Neural Network (CNN) model that can classify encrypted internet traffic. The model is trained with labeled FlowPic images build from the flow packets metadata (packet arrival time, packet length). This technology enables real-time traffic classification, once the model receives FlowPic image of a certain flow.
Programming Protocol-independent Packet Processor (P4) is a high-level language that can be deployed in the future into Software Defined Networks (SDN) and can actually serve as an alternative to OpenFlow that is currently used – due to its flexibility and ability program the data plane and support emerging new protocols.
In this project we will use Mellanox SN3700 P4-capable Spectrum-2 based switch. The P4 programmed switch will send to the collector, for a certain flow, its packet metadata. The collector will build FlowPic image and send it to the trained model for real-time flow classification.
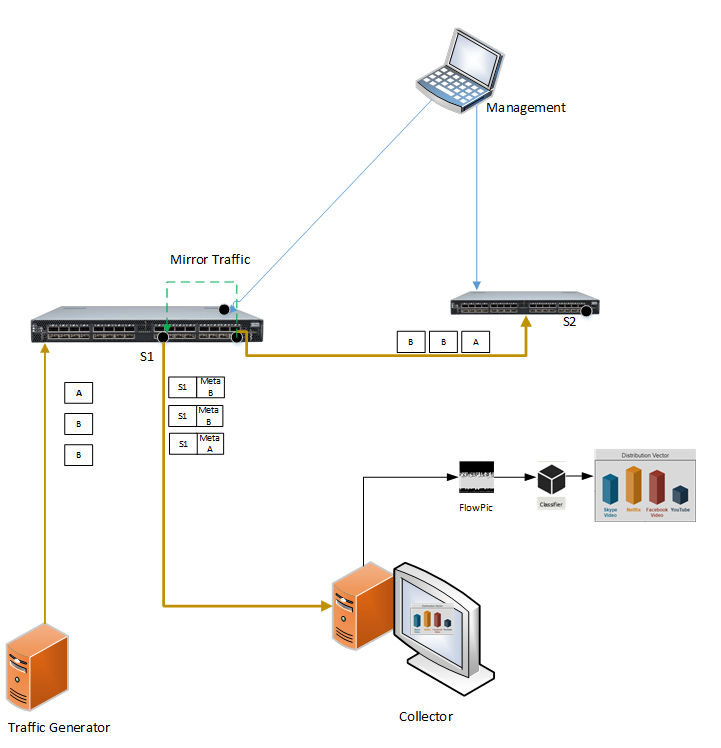
Project Title:
Deep Learning based Traffic Classification
Students:
Sahar Cohen, Ron Grinberg, Gil Zimmerman
Supervisors:
Aviel Glam (Rafael), Itzik Ashkenazi,
Description:
Traffic classification, the categorization of network traffic into appropriate classes, is important to many applications, such as quality of service (QoS) control, pricing, resource usage planning, malware detection, and intrusion detection. Because of its importance, many different approaches have been developed over years to accommodate the diverse and changing needs of different application scenarios. In particular, the growing trends of Internet traffic encryption and an increase Virtual Private Networks (VPNs) and The Onion Router (ToR) usage, raise additional challenges to network traffic classification.
Traffic classification techniques have evolved significantly over time. The first and easiest approach is to use port numbers. However, its accuracy has been decreasing because newer applications either use well-known port numbers to disguise their traffic or do not use standard registered port numbers. Despite its inaccuracy, the port number is still widely used either alone or in tandem with other features in practice. The next generation of traffic classifiers, relying on payload or data packet inspection (DPI), focuses on finding patterns or keywords in data packets. These methods are only applicable to unencrypted traffic and has high computational overhead. As a result, a new generation of methods, based on flow-statistics, emerged. These methods rely on statistical or time series features, which enable them to handle both encrypted and unencrypted traffic. These methods usually employ classical Machine Learning (ML) algorithms, such as random forest (RF) and k-nearest neighbor (KNN). However, their performance heavily depends on the human-engineered features, which limit their generalizability.
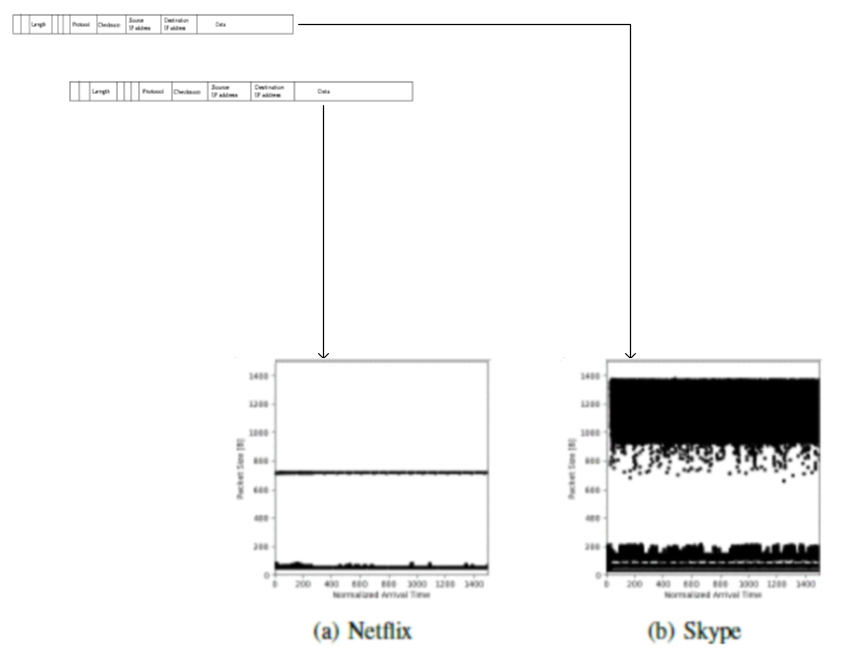
Project Title:
MPEG-DASH Live Streaming in Unstable Environment
Supervisors:
Aviel Glam (Rafael), Itzik Ashkenazi,
Description:
MPEG-DASH (Moving Picture Experts Group - Dynamic Adaptive Streaming over HTTP) is a vendor independent, international standard ratified in 2012. One of the main benefits of MPEG-DASH is reduction of startup delays and buffering/stalls during the video and continued adaptation to the bandwidth situation of the client.
Today, MPEG-DASH is gaining more and more deployments, accelerated by services such as Netflix or Google, which recently switched to this new standard. With these two major sources of internet traffic, 50% of total internet traffic is already MPEG-DASH.
The basic idea of MPEG-DASH is as follows: chop the media file into different bitrates or spatial resolutions encoded segments. The segments are provided on a Web server and can be downloaded through HTTP standard compliant GET requests where the HTTP Server serves different qualities, chopped into segments of equal length. Since the client knows its capabilities, received throughput and the context of the user best - the adaptation to the best bitrate or resolution is done on the client side for each segment.
In previous semester, we managed to achieve MPEG-DASH live streaming (sub 2 second delay) in an un-stable environment by improving the client’s rate adaptation algorithm. The traffic instability was simulated by Netem tool. In this project we will use MiniNet-WiFi that will emulate WiFi mobile clients and will research the MPEG-DASH client rate adaption in various mobility models
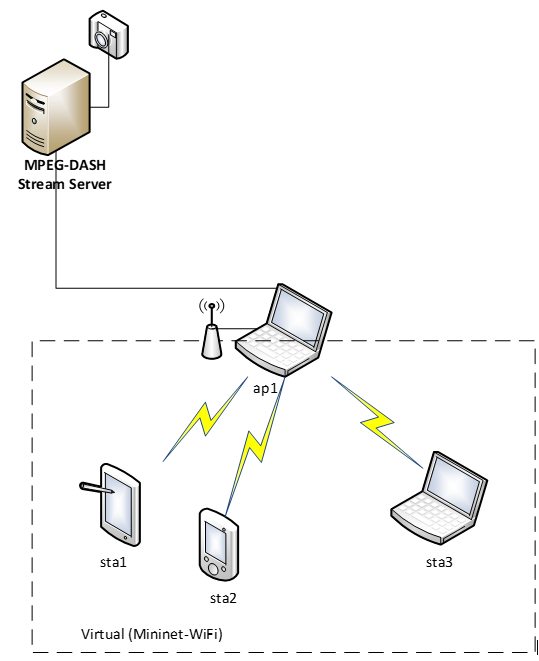
Project Title:
Intelligent End-To-End Traffic Congestion Trouble Shooting – using P4
Students:
May Elbaz, Adi Sharon
Supervisors:
Alan Lo (Mellanox), Itzik Ashkenazi
Description:
Programming Protocol-independent Packet Processor (P4) is a high-level language that can be deployed in the future into Software Defined Networks (SDN) and can actually serve as an alternative to OpenFlow that is currently used – due to its flexibility and ability program the data plane and support emerging new protocols.
Debugging End-To-End traffic problems and finding the root cause for packets congestion or un-expected high End-To-End latency plays a significant role in network management. Trouble shooting such issues in order to find the root cause, especially in a Data Center where traffic volume is massive, can be a difficult task.
In this project we will use Mellanox SN3700 P4-capable Spectrum-2 based switches and implement an online intelligent method, based on postcard telemetry, that will debug end-to-end traffic congestion or high latency events and will pinpoint its root cause.
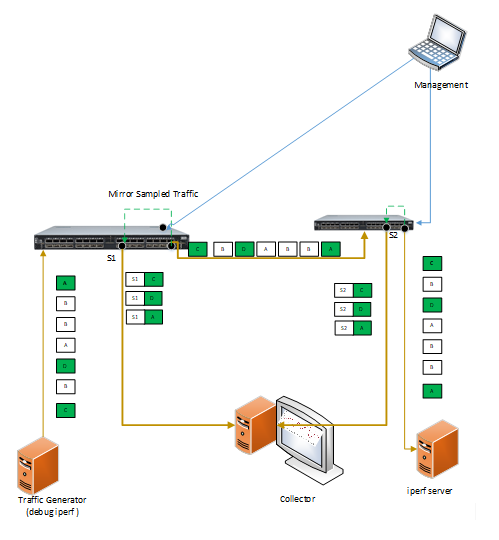
Project Title:
Smart Mobile LoRaWAN Gateway
Supervisors:
Aviel Glam (Rafael), Itzik Ashkenazi,
Description:
Low-power WAN (LPWAN) is a wireless wide area network specification that interconnects low-bandwidth, battery-powered sensors with low bit rates over long ranges.
To meet the challenges of long range, low power consumption and secure data transmission, the sensors are based on LoRa Technology and on LoRaWAN media access control (MAC) layer protocol that manages communication between LPWAN sensors and the Gateway.
Not in all circumstances its possible for an end node sensor to communicate with the outside world. This requires to use mobile gateway utilized on drone. The drone on its flight path can reach the remote location where the sensor device is running and collect its data. The challenge in this solution is to establish a communication link with every sensor node, by being at the correct location at the right sensor duty cycle time.
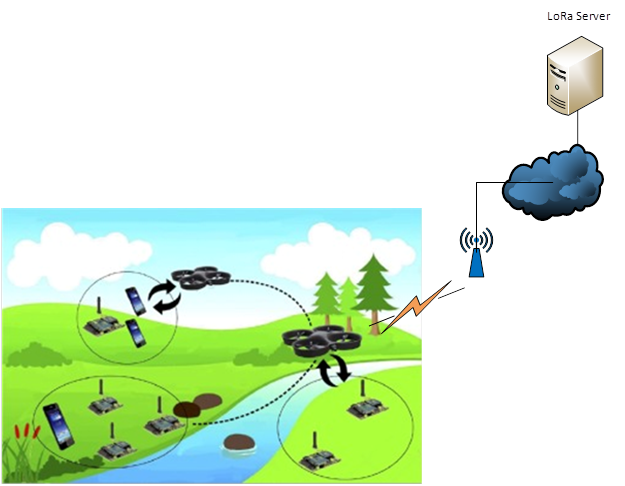
Project Title:
Malware Detection in NFV Edge Computing - using Machine Learning
Supervisors:
Andrew Sergeev (Adva), Itzik Ashkenazi
Description:
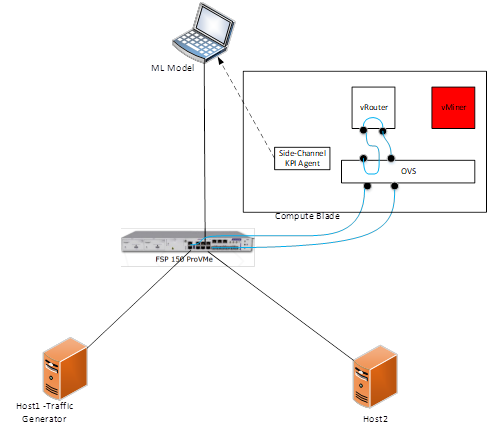
Network Function Virtualization (NFV) is an emerging approach gaining popularity among network providers. NFV takes the physical networking devices commonly used today (switches, routers, load balancers, firewalls, antivirus, storage devices etc.) and visualizes them in the cloud.
Edge computing provides these compute and storage resources with adequate networking connectivity close to the devices generating traffic. The benefit is the ability to provide new services with very low latency and avoid the data travel far in the network to reach the server in the cloud.
The ADVA FSP-150 proVMe is a Multi-layer demarcation device that is equipped with a compute blade, based on x86 architecture CPUs, for NFV hosting. It is located in the cloud edge at the customer premise or at the cell site.
However, along with its flexibility, this approach inherits the vulnerabilities of CPU architecture.
It allows an attacker to obtain root privileges and to plant malware. Among such malware is crypto mining that is stealing CPU cycles from a legitimate NFV application. Such malware is hardly detectable either by malware scanner or by a firewall.
In this project, we will use Machine Learning tools to investigate the applicability of side-channels Key Performance Indicators (KPIs) needed for malware detection.