2022
Project Title:
IOT L3 Router based on Raspberry Pi and P4
Supervisors:
Eran Tavor
Description:
Routers are traditionally very expensive and complicated devices. In this project you will develop a modern layer 3 router using a novel Switch programmable language (P4). The hardware of the router is based on RaspberryPi 4 Single Board Computer(SBC) and the software is based on the P4 open source compiler T4PAS.
The Router’s design is separated to a Data Plane – programmed in P4 and a Control Plane – programmed in python.

Project Title:
Ethereum Blockchain Mempool Activity Recorder
Supervisors:
Avi Mizrahi, Eran Tavor
Description:
The popularity of cryptocurrencies, such as Bitcoin and Ethereum, attracts attention to their underlying technology, the Blockchain. A Blockchain is a databases based on chain of blocks, and each block is composed of set of transactions. To form a new block at the top of the chain, nodes in the system share new transactions between them, until one of them can pack a set into new block. For that, nodes in the network maintain a local pool of pending transactions, usually called mempool. Mempool synchronization takes major part of the network bandwidth, hence it is valuable to find an efficient algorithm for it.

Project Title:
IoT LoraWAN Cyber Attacks Avoidance
Supervisors:
Maayan Hacohen, Aviel Glam, Eran Tavor
Description:
Low-power WAN (LPWAN) is a wireless wide area network specification for Internet-of-Things (IoT)
deployments that interconnects low-bandwidth, battery-powered sensors with low bit rates over long
ranges.
To meet the challenges of long range, low power consumption and secure data transmission, the sensors
are based on LoRa Technology and on LoRaWAN media access control (MAC) layer protocol that manages
communication between LPWAN sensors and the Gateway.
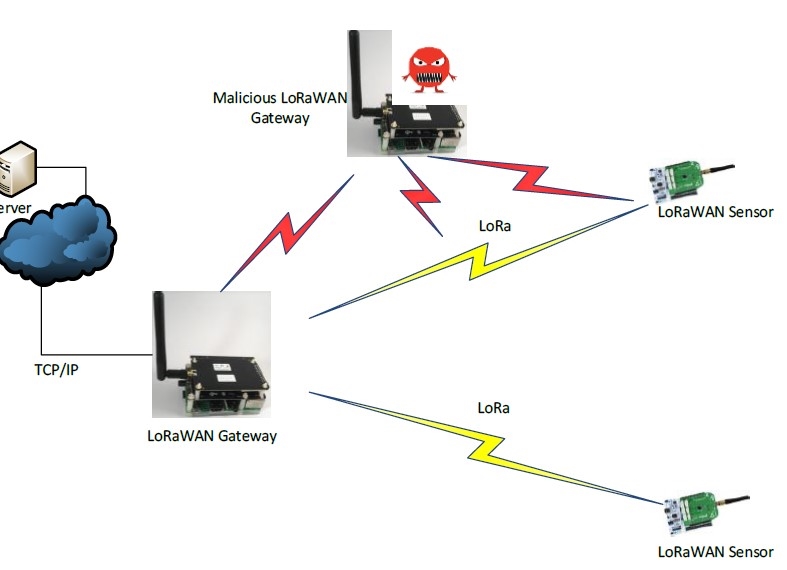
LPWAN based LoRaWAN is vulnerable to 2 cyber attack types: Malicious Gateway and sensor flooding
attack. Malicious LoRaWAN Gateway can track the sensors-gateway downlink-uplink traffic pattern and
then disrupt the traffic. Sensor flooding attack can be generated by multiple coordinated malicious
LoRaWAN sensors that can generate traffic simultaneously and so cause the LoRaWAN server to mal
function. LoRaWAN gateways should be able to a. self-detect such attacks and b. avoid LPWAN collapse
by notifying sensors to change their frequency of operation.
Project Title:
QUIC RTT estimation without Latency Spin Bit
Supervisors:
Eran Tavor
Description:
QUIC is a secure general-purpose, encrypted, multiplexed, and low-latency transport protocol designed from the ground up to improve transport performance for HTTPS traffic. QUIC has recently (May 2021) became RFC standard (RFC 9000) and is expected to become the dominant transport protocol in the Internet over TCP. Most of QUIC packets are encrypted. Not only the payload is encrypted but also most of the header. This situation makes it very difficult for the ISP (Internet Service Provider) ir any middlebox to monitor the network and enforce regulatory measures to keep the network up and running. One important parameter for ISPs to monitor network health is RTT estimation. When RTT rise too high for many flows it may indicate that queues build-up and an up-coming network collapse. In such situations the ISP may limit heavy users and keep the network alive. Therefore, an efficient estimation of RTT is an important network management. As QUIC is almost fully encrypted, there are only few unencrypted bits, one of then is the latency spin bit that intentially left unencrypted for RTT estimation. The use of the Latenct Spin bit is not mandatory. Former project implemented a mechanism to measure RTT using the Latency Spin bit. This projects aims at doing this task without the use of the Latency Spin bit.

Project Title:
QUIC Connections Cardinality Estimator Using Sketch
Supervisors:
Eran Tavor
Description:
QUIC is a secure general-purpose, encrypted, multiplexed, and low-latency transport protocol designed from the ground up to improve transport performance for HTTPS traffic. QUIC has recently (May 2021) became RFC standard (RFC 9000) and is expected to become the dominant transport protocol in the Internet over TCP. In this project the student will use a previously developed QUIC sniffer and implement an efficient tool that estimates efficiently the cardinality of QUIC connections (how many different QUIC connections can be observed) using a statistical estimator (a Sketch).

Project Title:
NVIDIA P4 Runtime Smart classification
Supervisors:
Idan Barnea, Matty Kadosh, Aviel Glam, Eran Tavor
Description:
The goal of this project is to develop a live AI-based firewall.
In this project you will deploy the P4Runtime software package on a high-performance switch (25+ Gigabits per second) and use AI to create a live firewall.
The system that you will build will do the following:
1. Extract data at a high rate from the switch and deliver it to an AI engine
2. Classify the data with an AI algorithm
3. Act according to the AI classification: add/delete entries to the tables in the switch. This part will use the new P4Runtime engine
4. Drop/pass packets according to the classification. This is the goal of the firewall
The project’s outcome will probably be one of the first AI-based firewalls that run in real-time.
Project Title:
Traffic Performance Prediction using ML
Supervisors:
Eran Tavor
Description:
Mobile communication networks are subject to dynamics in topology, transmission rates, and clients’ demands (in terms of transmission rates and latency), In order to manage such complex network and allocate its resources to maximize end user quality of experience, we need an optimization tool that will be able to predict the traffic bandwidth or the latency performance once the network topology changes or a new application starts running. Developing such a tool requires network modeling. Nowadays, network models are either based on packet-level simulators or analytical models (e.g., queuing theory). Packet–level simulators are very costly computationally, while the analytical models are fast but not accurate. Hence, Machine Learning (ML) arises as a promising solution to build accurate network models that are able to operate in real time and to predict the resulting network performance according to the target policy, i.e., maximum bandwidth or minimum end-to-end latency.