2016
Project Title:
Supporting Built-in Monitoring Agents in Mininet
Description:
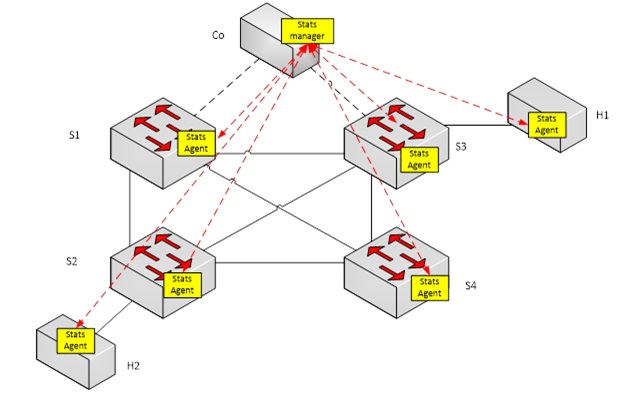
Mininet is a system for rapidly prototyping large networks on the constrained resources of a single laptop. Mininet makes it easy to interact with your network using CLI and API, making it a great way to develop, share and experiment with OpenFlow and Software-Defined Networks.
Network traffic monitoring is a critical building block in various management, control and security applications. Analysis of monitoring data provides important information like trends in network load and utilization, performance of traffic engineering systems, or security vulnerability.
Deploying a network wide efficient monitoring algorithms usually requires deploying monitoring agents (either reactive or proactive) on various nodes, an ability that Mininet currently lacks.
Project Title:
Billing For Smart Parking Project – Using Matrix.Org
Description:
One of the fundamental requirements from a Smart Parking implementation is its ability to perform billing for the parking usage. This can be achieved by connecting the Smart Parking Manager (SPM) to private parking applications such as Pango or CelloPark.
The connection between PSM and the applications can be done using Matrix (http://matrix.org/). Matrix is an open standard for interoperable, decentralized, real-time communication over IP. Matrix defines the standard, and provides open source reference implementations of Matrix-compatible Servers, Clients, Client SDKs and Application Services to allow anyone to create new communication solutions or extend the capabilities and reach of existing ones.

Project Title:
Internet-of-Things (IoT) Gateway with Network Address Translation (NAT) support - For Smart Campus Project
Description:
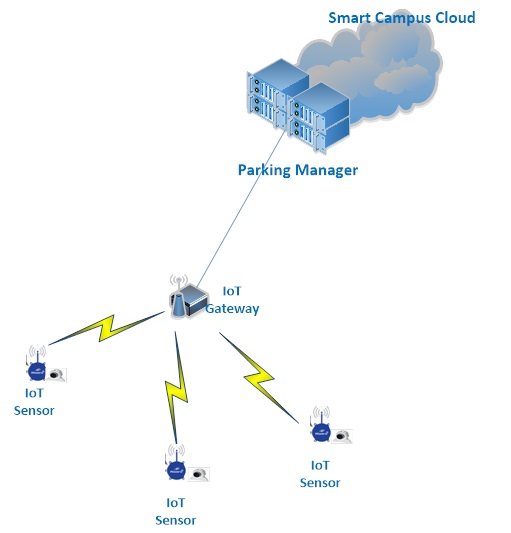
One of the fundamental requirements from a Smart Campus Transportation implementation and deployment is the ability of the campus to take responsibility and globally manage the traffic as whole inside the campus physical boundaries. This management should then serve both campus applications (such as events organizations or security needs) as well as guests that enters or plans to arrive. This can be achieved by improved monitoring and ability to supply on-line valuable information gathered from private mobile platforms like Waze, Moovit , Hoover and more, as well as from web cams and Internet-of-Things (IoT) sensors that are installed all over the campus area.
The target of an IoT Gateway is to collect all information arrives from the IoT sensors as well from the Web cams, and transfer this data up to the application manager that resides in the cloud. In certain cases the gateway should be able also to support down-stream traffic to the sensors and to other peripheral devices.
Project Title:
BGP Prefix Hijacking Attack Investigation
Description:
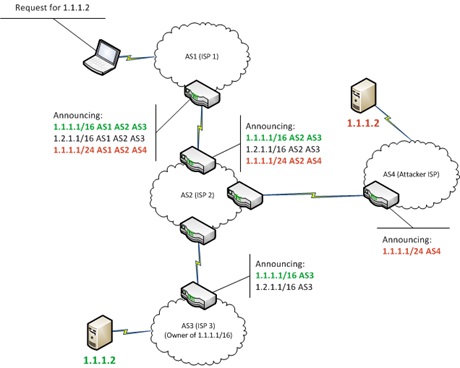
The Internet infrastructure was not designed with security in mind, and is consequently alarmingly vulnerable. It is based on Border Gateway Protocol (BGP) which performs the routing between administrative domains, or “Autonomous Systems” (ASes) , and is considered as an insecure protocol.
One of the known attack on BGP is BGP hijacking. Cybercriminals and governments alike have taken advantage of this technique for their own ends, such as traffic misdirection and interception. The hijacking is based on the fact that BGP determines how data flows from its source to its destination. By manipulating BGP, data can be rerouted according to the attacker’s choise, allowing them to intercept or modify traffic. Internet-level BGP hijacking is performed by configuring an edge router to announce prefixes that have not been assigned to it. If the malicious announcement is more specific than the legitimate one, or claims to offer a shorter path, the traffic may be directed to the attacker. Attackers will frequently target unused prefixes for hijacking to avoid attention from the legitimate owner. By broadcasting false prefix announcements, the compromised router may poison the Routing Information Base (RIB) of its peers, as shown below. After poisoning one peer, the malicious routing information could propagate to other peers, to other Autonomous Systems, and onto the broader Internet.
Project Title:
Flow Classification Open Virtual Switch (OVS) Offload
Description:
Today’s Carrier Ethernet architecture is undergoing the biggest transformation since the beginning of the internet. Video, mobile and cloud usage is driving huge growth in traffic while the constantly changing traffic patterns requires ability to introduce new services quickly. This led the creation of Networking Function Virtualization (NFV), which defines the specifications for Virtualized Network Function (VNF).
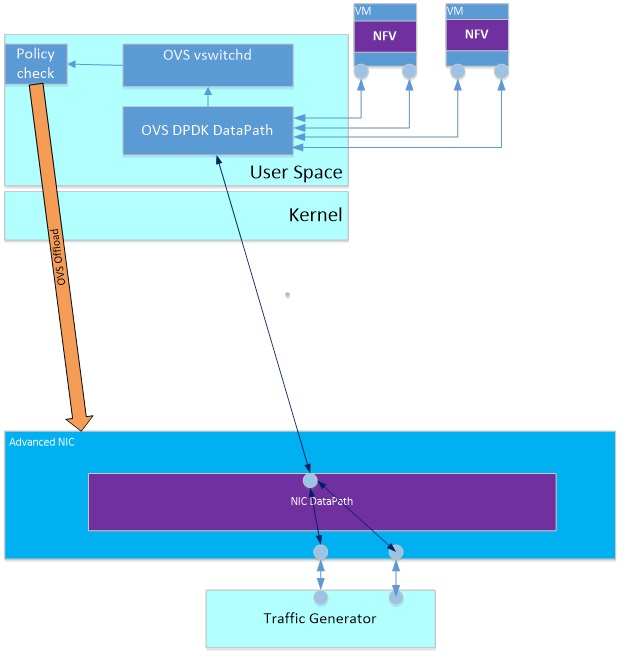
VNF is a software implementation of a network function such as routing or firewall. Each such VNF runs in a virtual machine (VM). The VMs are created in a compute blade or in a high scale server – unusually called the host device. The VMs are located on top of the host’s Hypervisor that uses Open Virtual Switch (OVS) to switch the data traffic to/from each VM/NFV and also to chain the traffic between them.
OVS is an OpenFlow switch and so the traffic switching is controlled by programming flows to its data plane engine. The flow determines the packet classification that will be done by the OVS data plane once a packet arrives. This classification is an expensive CPU operation since can involve hash table searches. Offloading part of the classification to an advanced NIC that will perform this operation in HW can improve significantly overall OVS performance.
Project Title:
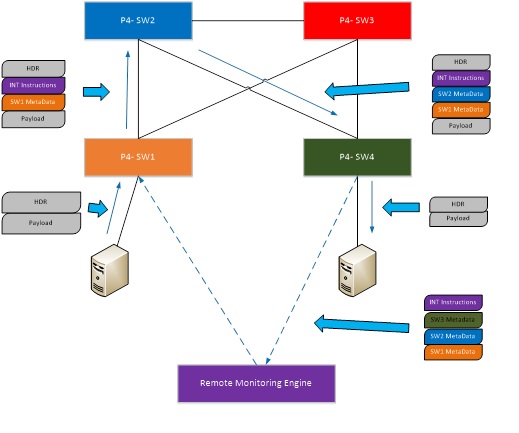
In-band Network Telemetry (INT) on Software Switch Programmed by P4
Description:
In-band Network Telemetry (INT) is a new framework designed to allow the collection and reporting of network state, by the data plane, without requiring intervention of additional control plane protocols. Data packets are instrumented with INT header fields that contain “Telemetry Instructions” to INT-capable network device. The instructions tell the devices what Telemetry data to collect and the collected data is written into the forwarded data packets.
INT data that can be collected includes: switch IDs, Input/Output Port IDs, Hop Latency, Queue Occupancy, In/Out Timestamps and more. Such telemetry data provides immense value in networks in general. It enables real-time debugging of network issues as well as “self healing” networks.
Programming Protocol-independent Packet Processor (P4) is a high-level language that can be deployed in the future into Software Defined Networks (SDN) and can actually serve as an alternative to OpenFlow that is currently used – due to its flexibility and ability to support emerging new protocols such as INT.
Project Title:
Distributed Denial of Service (DDoS) attack detection in a virtualized network
Description:
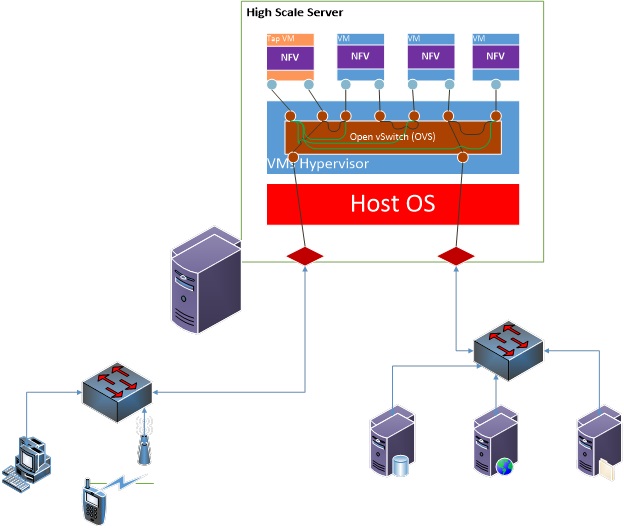
Today’s Carrier Ethernet architecture is undergoing the biggest transformation since the beginning of the internet. Video, mobile and cloud usage is driving huge growth in traffic while the constantly changing traffic patterns requires ability to introduce new services quickly. This led the creation of Networking Function Virtualization (NFV), which defines the specifications for Virtualized Network Function (VNF).
VNF is a software implementation of a network function such as routing or firewall. Each such VNF runs in a virtual machine (VM). The VMs are created in a compute blade or in a high scale server – unusually called the host device. The VMs are located on top of the host’s Hypervisor that uses Open Virtual Switch (OVS) to switch the data traffic to/from each VM/NFV and also to chain the traffic between them.
Distributed Denial of Service (DDoS) attack embedded in the data traffic can cause performance degradation to the OVS, NFVs as well as to the servers behind. A good sign for DDoS attack is an increasing or high rate of active data flows in each time slot – compared to normal or pre-defined number of flows threshold. In order to detect such case – it is required to have ability to estimate on-line the total number of flows per VM/NFV. The number of flows estimation can be done by analyzing sampled stream per VM/NFV.
Project Title:
ISP Mapping using RocketFuel Technique
Description:
Real Internet Service Providers (ISP) topologies today are not publicly available, since ISPs generally regard their router-level topologies as confidential. Some ISPs publish simplified topologies on the Web, but these lack router-level connectivity, Point-Of-Presence (POP) structure and are in most cases out of date.
The RocketFuel technique presents a measurement algorithm to infer high quality ISP maps while using as few measurements as possible. The RocketFuel is based on TraceRoute results and uses BGP routing information to choose only those traceroutes that are likely to transit the ISP being mapped. It also suppresses traceroutes that are likely to yield paths through the ISP network that have been already been traversed. These two techniques reduce the number of traces required to map an ISP by three orders of magnitude compared to a brute-force, all-to-all approach, without compromising on the accuracy.

Project Title:
Early DDoS Attack Detection by a Stateless Device
Description:
Detecting Distributed Denial of Service (DDoS) attacks by the router or the switch located in early stage before the attacked server can improve significantly the overall performance since the switch/router itself can trigger packet based filtering rules in order to reduce the load towards the servers.
A good sign for DDoS attack is an increasing or high rate of active flows in each time slot – compared to normal or pre-defined number of flows threshold. In order to detect such case – it is required from a stateless device to be able to estimate on-line the total number of flows while using small memory footprint. The number of flows estimation can be done by working and analyzing the entire stream or only on a sampled stream.

Project Title:
Restorable Logical Topology using Cross-Layer Optimization
Description:
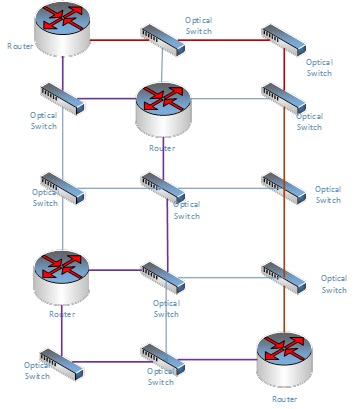
Today’s communication networks consist of routers and optical switches in a logical topology overlaid on an optical physical infrastructure. The routers are connected to each other via logical links called LightPaths, where each LightPath is established over one or more optical fibers and optical switches connecting these fibers.
The design of LightPaths involves selection of both logical link and logical path, i.e decision which pairs of routers will be connected by the LightPaths and how to route each LightPath across the optical network. Such design requires cross-layer optimization that will maximize the end-to-end traffic throughput in case of a physical failure in order to guarantee the restorability of the logical topology.
Project Title:
DDoS Detection with P4
Students:
Yulia
Supervisors:
Itzik A



